EXECUTIVE SUMMARY
Researchers has recently uncovered a new version of JSOutProx, a sophisticated attack framework that targets financial services and organizations primarily in the Asia-Pacific (APAC) and Middle East-North Africa (MENA) regions. This advanced malware employs both JavaScript and .NET, utilizing the .NET (de)serialization feature to interact with a core JavaScript module on the victim's machine. Initially attributed to SOLAR SPIDER's phishing campaigns in 2019, JSOutProx RAT infiltrates financial institutions across Africa, the Middle East, South Asia, and Southeast Asia. Recently, Researchers identified a surge in activity around February 2024, with multiple victims targeted through GitHub and GitLab repositories, indicating an evolution in the actor's tactics.
JSOutProx exhibits a multi-stage infection chain, with payloads disguised as legitimate files such as PDFs, utilizing masquerading techniques to evade detection. The malware facilitates remote access to compromised systems, enabling malicious activities like executing shell commands, handling file operations, capturing screenshots, and controlling keyboard and mouse actions. Notably, it utilizes Dynamic DNS for command and control (C2C) communication, employing the Cookie header field for information transmission. Moreover, the malware's modular architecture supports various plugins, enhancing its capabilities for data theft, proxy manipulation, clipboard monitoring, and privilege escalation. The recent shift to GitLab indicates a strategic adaptation by threat actors to diversify their infrastructure and maintain operational security.
The emergence of the new JSOutProx variant underscores the persistent threat posed by sophisticated cybercriminals, particularly to financial institutions and organizations in the APAC and MENA regions. Despite ongoing efforts by security researchers to disrupt these campaigns, the evolving tactics and infrastructure of threat actors highlight the need for continuous vigilance and proactive defense measures. As malicious activities escalate in complexity and scope, collaboration between cybersecurity experts, law enforcement agencies, and targeted entities becomes increasingly crucial to mitigate the impact and safeguard against future threats.
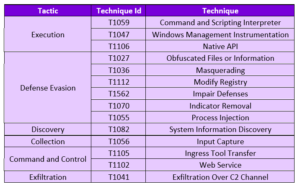
THREAT PROFILE:
REFERENCES:
The following reports contain further technical details:
https://thehackernews.com/2024/04/new-wave-of-jsoutprox-malware-targeting.html