Summary:
A concerning trend has emerged in the form of a continuous phishing campaign targeting both the cryptocurrency community and healthcare organizations across the United States. This sophisticated campaign employs various tactics, including subdomain takeover and the misuse of legitimate remote support tools like ScreenConnect by ConnectWise Inc. The attackers lure unsuspecting users to phishing sites where they download malicious files disguised as cryptocurrency-related offers or healthcare services. Once compromised, these systems become vulnerable to further exploitation, potentially leading to data breaches, malware deployment, and other malicious activities. Recent disclosures have highlighted significant vulnerabilities within ConnectWise's ScreenConnect software, designated as CVE-2024-1708 and CVE-2024-1709. These flaws pose grave security risks, potentially enabling unauthorized access and control by malicious actors and leading to severe disruptions such as ransomware attacks.
Analysis of the ScreenConnect client reveals a systematic method employed by threat actors to illicitly access victim systems. Upon execution, the client installs a Microsoft Installer file, deploying the ScreenConnect service on the victim's machine. Embedded launch parameters within the client service enable communication with the attackers' server, facilitating session initiation and potentially enabling data extraction or further malware deployment. Despite observed instances lacking active communication, the threat remains severe, indicating potential for future cyber operations. Despite law enforcement actions, attacks persist, leveraging vulnerabilities to introduce diverse payloads into business environments, including ransomware such as LockBit, AsyncRAT, password stealers like Vidar/Redline, and remote access clients like SimpleHelp. Threat actors leverage ScreenConnect for executing commands, downloading payloads, and maintaining persistence on compromised systems. CVE-2024-1708, a path-traversal vulnerability, and CVE-2024-1709, an authentication bypass vulnerability, together facilitate full remote code execution on affected systems. The authentication bypass vulnerability arises from a path problem in ScreenConnect.Web.dll's SetupModule, allowing unauthorized account addition and code execution. Meanwhile, the path-traversal vulnerability originates from improper validation of user-supplied paths in ScreenConnect.Core.dll, leading to directory traversal via ZipSlip attacks. These vulnerabilities are actively exploited by threat actor groups, such as Black Basta and Bl00dy Ransomware, employing tactics ranging from reconnaissance to ransomware deployment, underscoring the critical importance of patching and securing vulnerable systems.
In conclusion, the recent surge in ScreenConnect usage underscores the critical need for heightened cybersecurity measures across all sectors, particularly within healthcare organizations. The exploitation of legitimate software for nefarious purposes highlights the evolving nature of cyber threats and emphasizes the imperative for robust defenses. Such attacks not only result in financial losses but also pose substantial risks to patient safety, privacy, and essential healthcare services. To effectively mitigate these risks, organizations must prioritize comprehensive cybersecurity protocols, including regular security assessments, thorough employee training, and the adoption of advanced threat detection and response mechanisms. Urgent action is required to assess and mitigate exposure, including isolating or uninstalling client software, conducting detailed analyses for suspicious activities, and implementing incident response plans, as necessary. Proactive management of software updates is crucial for bolstering cybersecurity defenses against evolving threats.
Recommendations:
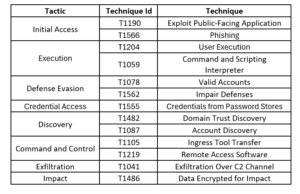
Threat Profile:
References:
The following reports contain further technical details:
https://news.sophos.com/en-us/2024/02/23/connectwise-screenconnect-attacks-deliver-malware/