Summary:
The 8220 Gang, also known as the "8220 Mining Group," has been active since 2017 and focuses on exploiting vulnerabilities in cloud and container environments. They have targeted various applications, including Oracle WebLogic, Apache Log4j, Atlassian Confluence, and misconfigured Docker containers, to deploy cryptocurrency miners on both Linux and Windows systems. The gang utilizes tools such as Tsunami malware, XMRIG cryptominer, masscan, and spirit in their campaigns.
Recent research indicates that the threat actor has been active in recent months. One attack observed targeted the Oracle WebLogic vulnerability CVE-2017-3506. This vulnerability allows attackers to execute arbitrary commands remotely through a specifically crafted XML document, potentially compromising sensitive data or the entire system. The entry point for this attack was the HTTP URI which was used to target Oracle WebLogic servers. The gang delivered a PowerShell script that exploited the six-year-old vulnerability, creating other dropper files. Notably, the group also targeted Windows systems using the Linux utility "lwp-download."
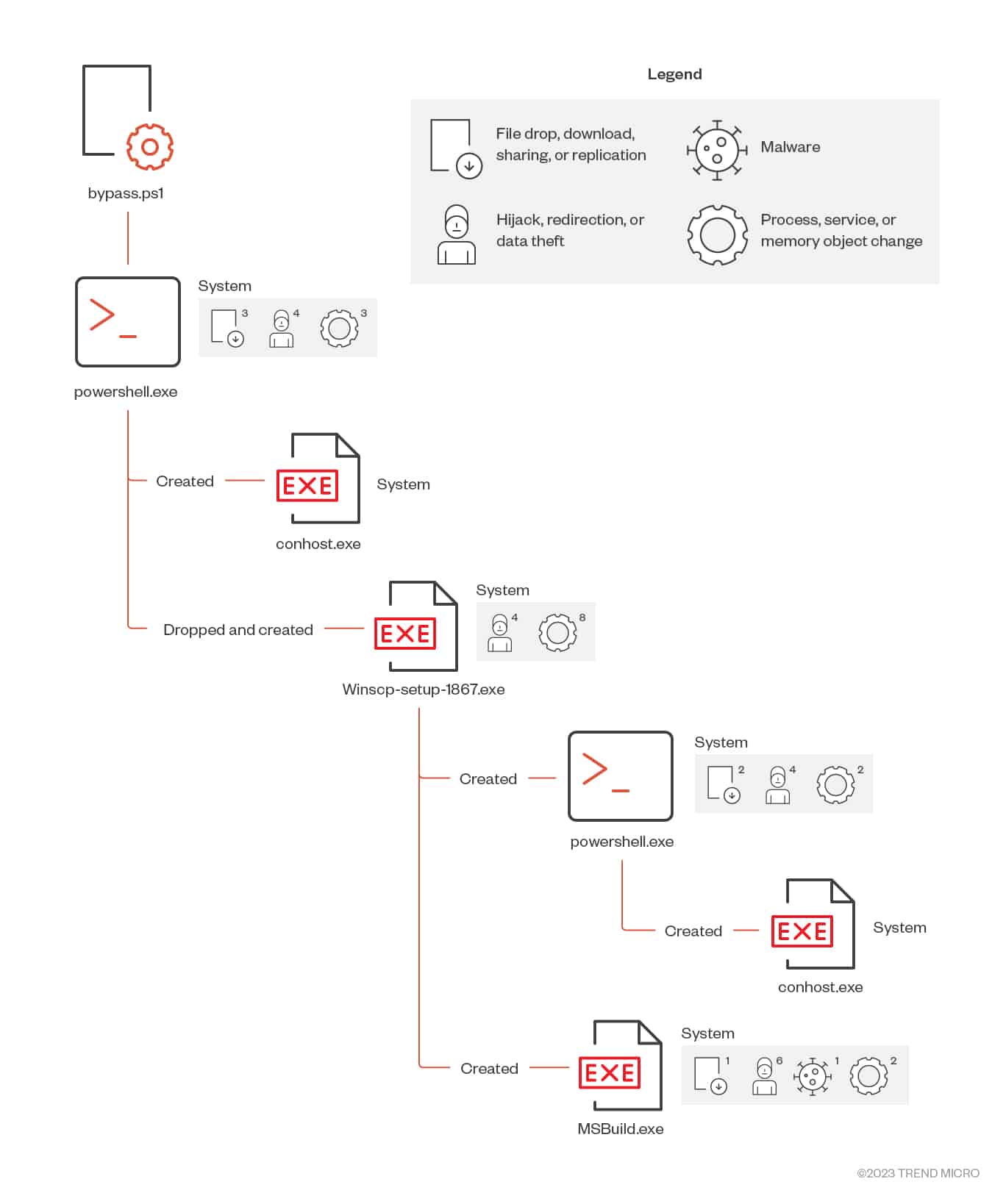
Execution Flow
The attack payload involved executing a PowerShell command encoded with Base64. After decoding, the command opened a hidden PowerShell window, bypassing execution policies. The decoded command downloaded and executed a PowerShell script without displaying any visible output to the user. The script disabled the AMSI detection, wrote a malicious binary file in the Windows "temp" directory, and executed it without displaying any user interface. The file "Winscp-setup-1867.exe" was responsible for continuously sending GET requests to its server, downloading the file "Ebvjmba.dat" from the C&C server. The DLL file contacted the file server and downloaded the DAT file dropper. The newly created DLL file was an encrypted resource file injected into the MS Build process. After inspecting the process's memory, it was found that the injected payload communicated with C&C servers on TCP ports to download a cryptocurrency miner.
The gang's use of the Linux utility "lwp-download" poses a significant challenge for security teams, as it can affect multiple services and platforms. The gang's tendency to reuse tools and abuse legitimate utilities complicates detection and blocking efforts. Despite being labeled as "low-level script kiddies" by some researchers, the 8220 Gang poses a significant threat. They have evolved from using simple and easily detectable scripts to employing more damaging malware in their campaigns. Organizations need to stay updated with security patches and strengthen their security systems to defend against these attacks.
Recommendations:
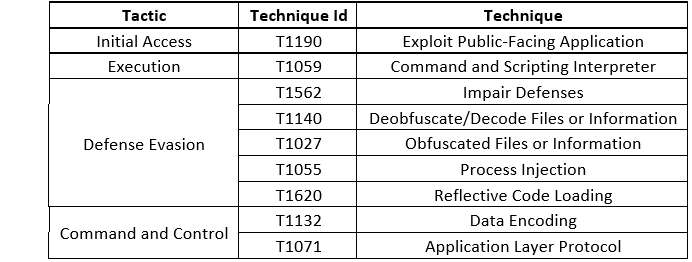
Threat Profile:
References:
The following reports contain further technical details:
https://www.trendmicro.com/en_us/research/23/e/8220-gang-evolution-new-strategies-adapted.html