Summary:
In the rapidly evolving landscape of cybersecurity, adaptability is no longer just desired, but necessary for survival. Recently, the banking industry has faced a new and concerning type of cyber threat, where it became the explicit target of two distinct open-source software supply chain attacks. The threat actor exploited the NPM platform by uploading packages containing a preinstall script that executed malicious actions upon installation. Notably, the contributor behind these packages was linked to a LinkedIn profile page, posing as an employee of the targeted bank. Surprisingly, when contacted, the bank had no knowledge of this activity.
The attack unfolded in multiple stages. Initially, the script identified the victim's operating system and decoded encrypted files included in the NPM package accordingly. Subsequently, the decoded files facilitated the download of a second-stage malicious binary onto the victim's system. The attacker customized the malware to avoid detection, especially on Linux systems, where VirusTotal failed to flag the Linux-specific encrypted file as malicious. Furthermore, the attacker exploited legitimate domains, specifically Azure's CDN subdomains, to deliver the second-stage payload. By cleverly incorporating the targeted bank's name in the subdomain, the attacker increased the chances of a successful breach. The attacker utilized the Havoc Framework as their tool of choice for the second stage, enabling them to evade standard defenses and maintain control over compromised systems.
A while after that, a different bank fell victim to cybercriminals with their own unique strategies. The attackers uploaded a package to NPM, containing a carefully crafted payload that blended seamlessly into the victim bank's website. The malicious code laid dormant until triggered into action. The payload targeted the bank's mobile login page by identifying a specific login form element in the HTML. It then stealthily intercepted login data and transmitted it to a remote location, exposing the bank's users to potential compromise.
These attacks highlight the urgency for organizations to shift their supply chain security strategy. Traditionally, vulnerability scanning at the build level was the primary focus, but with advanced cyber threats, such measures are no longer sufficient. Once a malicious open-source package enters the pipeline, it instantaneously breaches the system, rendering subsequent countermeasures ineffective. Therefore, organizations must adopt a proactive and integrated security architecture, implementing protective measures at every stage of the Software Development Lifecycle (SDLC) to prevent infiltration of malicious packages.
With a steady escalation of targeted attacks on banks and other industries, it is crucial to shed light on the Tactics, Techniques, and Procedures (TTP) observed in these emerging threats. Staying vigilant, continuously evolving defenses, and remaining a step ahead of threat actors is the need of the hour. Organizations must take proactive steps to secure their supply chains and protect their assets, users, and data from malicious attacks.
Threat Profile:
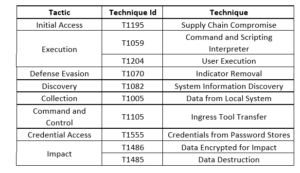
References:
The following reports contain further technical details:
https://thehackernews.com/2023/07/banking-sector-targeted-in-open-source.html