Summary:
Researchers uncovered two distinct cyber campaigns, dubbed "Contagious Interview" and "Wagemole," both attributed to North Korea state-sponsored threat actors. These campaigns target job-seeking activities, especially among software developers, using fraudulent job offers and interviews to distribute malware. The Contagious Interview campaign orchestrated by North Korea's state-sponsored threat actors unfolds with a strategic focus on software developers. They assume the guise of prospective employers through job platforms or direct communication, luring developers into online interviews. Wagemole focuses on fake job applications with fabricated identities seeking remote IT jobs in the US and globally. The malware discovered, BeaverTail and InvisibleFerret, serve as sophisticated cross-platform tools, reinforcing the threat actors' objectives of theft and potential espionage. Contagious Interview is tracked by researchers under CL-STA-0240, whereas Wagemole is tracked under CL-STA-0241.
BeaverTail, embedded within the NPM package, operates with a dual role. First, it functions as an information stealer, targeting cryptocurrency wallets and credit card data stored within web browsers. Second, it acts as a loader, executing InvisibleFerret, a Python-based backdoor with cross-platform capabilities. InvisibleFerret boasts multifaceted functionalities: collecting system information and sending it in JSON format to a command and control (C2) server, conducting remote control operations, including keylogging for capturing keyboard, mouse, and clipboard data, and pilfering browser data for login credentials and credit card information. Exploiting GitHub's service, the threat actors set up single-repository accounts with minimal updates to distribute malware, capitalizing on unsuspecting developers seeking genuine software.
On the other front, Wagemole, another North Korean-backed campaign, operates through fabricated identities and fictitious job applications aimed at US companies and the global freelance job market. The documents uncovered in this campaign, including bogus resumes, interview scripts, and stolen identities portraying individuals from diverse nationalities, allude to a strategic intent of funnelling wages into North Korea's weapons programs through remote work earnings.
Both campaigns exhibit tactics consistent with past North Korean APT activity. Contagious Interview specifically targets developers via GitHub and NPM, exploiting their reliance on third-party packages. Wagemole seeks remote IT jobs using false identities, indicating North Korea's intent to leverage remote workers for financial gain. Recommendations include vigilance in job applications, avoidance of installing files from unverified sources, and caution during online interviews.
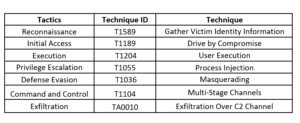
Threat Profile:
References:
The following reports contain further technical details:
https://thehackernews.com/2023/11/north-korean-hackers-pose-as-job.html