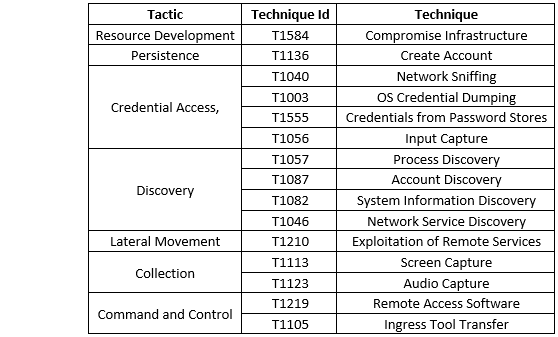
Summary:
The Daggerfly (also known as Evasive Panda, Bronze Highland) APT group appears to have recently targeted a telecoms company in Africa, and its most recent campaign utilised never-before-seen plugins from the MgBot malware framework. The attackers were also observed abusing the legal AnyDesk remote desktop software and using a PlugX loader. The initial indications of suspicious activity on the victim network targeted by this current Daggerfly activity included suspicious AnyDesk connections discovered on a Microsoft Exchange mail server. On the same Exchange server, the WannaMine crypto-mining malware was also discovered, though it seems likely that this activity was unrelated to the Daggerfly organisation. The PlugX loader was side loaded onto victim computers using the legal, free Rising antivirus programme.
BITSAdmin and PowerShell were technologies used by threat actors to download files onto victim systems. To obtain the usernames and passwords of online services stored in the credential manager using PowerShell, the attackers downloaded the genuine AnyDesk application as well as the GetCredManCreds programme. Additionally, they used the reg.exe utility to dump the Windows registry's SAM (Security Account Manager), System, and Security hives. As a result, the attackers were able to retrieve credentials from the SAM database. Additionally, Daggerfly set up a local account to keep access to the victim systems. The MgBot plugins used in this activity offer a variety of features that can provide the attackers access to a substantial amount of data about affected devices.
As a result of the possible access that telecommunications companies may have to end-user communications, they will always be a major target in intelligence collecting operations. The creation of MgBot plugins by Daggerfly shows that the attack organisation is still actively working on developing its malware and the resources it can utilise to target victim networks.
Threat Profile:
References:
The following reports contain further technical details:
https://thehackernews.com/2023/04/daggerfly-cyberattack-campaign-hits.html