Summary:
The APT group has been active since 2016 and seeks private and confidential information. Their attacks target both Windows and Android operating systems using YTY harmful frameworks and specially crafted Android APKs. The group regularly upgrades their malicious software to evade detection or other defenses.
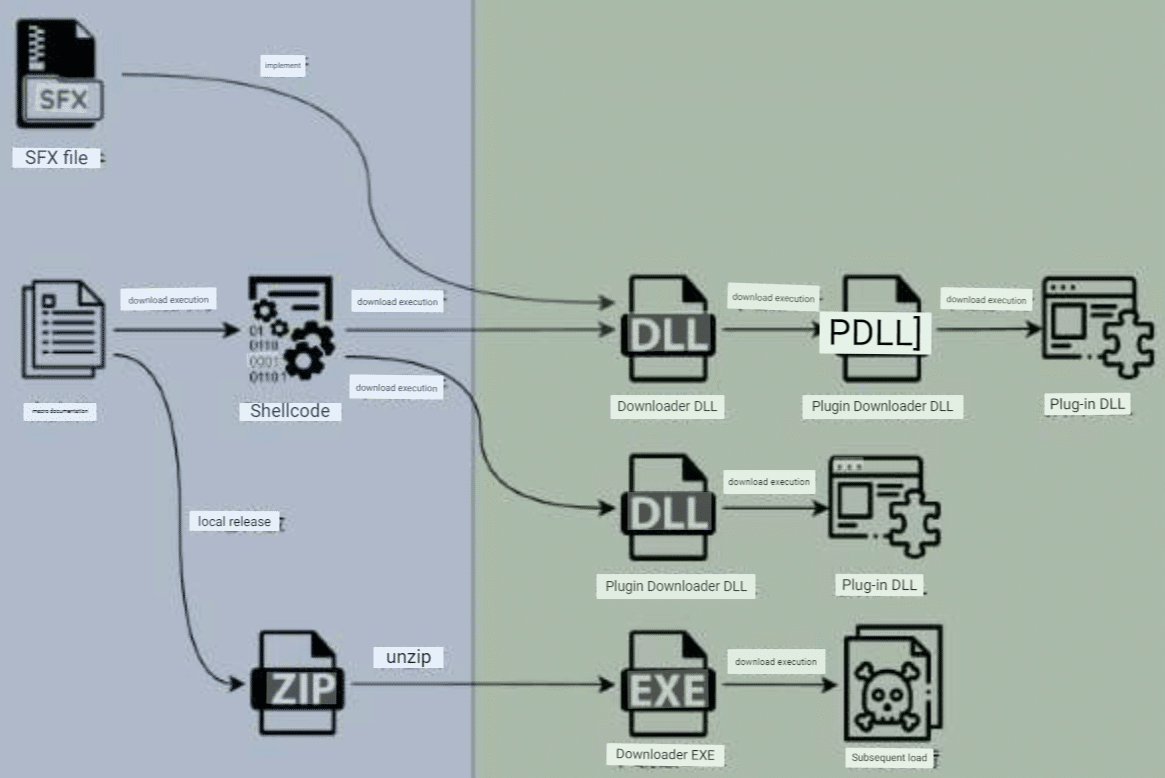
The Donot group frequently uses macros in documents to execute shellcode and download additional DLL components. These DLLs have the ability to download additional harmful components, including Trojan plugin managers and Trojan plugins. Attackers supply downloader DLL components directly through self-extracting RAR packages in attack samples that use documents about the Kashmir region as their lure. Additionally, in some attack efforts, the Donot group employs EXE components to download other components, which are directly released from compressed packages using macro documents.
Execution Flow
The attackers create malicious files, with the initial downloader attempting to download a file to "aco.bat" from specified URLs. The downloader encodes the string and creates an event named "ammonia", with extensive annotations on the VBA code. The sample releases pkhfg.bat, which creates three scheduled tasks to prepare for executing succeeding components. The tbreah.bat file extracts the downloader component dfer.exe from the dfer[.]cab file, after which it deletes the task via the "fghru" scheduled task. The executable component's code downloads two additional components from C2 in a specific order controlled by a global variable. The VBA code for creating scheduled tasks corresponds to the bat file location. Donot constantly encrypts critical strings in PE-based attack component parts using a variety of encryption techniques. That DLL components that have recently appeared frequently use double transformations and proprietary multi-layer encryption to disguise essential strings, in addition to simple addition or subtraction of present numerical values and single transformations. In addition, hackers can process separate strings using two encryption techniques.
The Donot group's tactics for attacking are largely fixed, and one common method in their attack chain is connecting sequential components with scheduled operations. The gang is, however, also expanding its attack tactics, using more inventive techniques for introducing malicious components and utilizing a variety of components. while there haven't been any instances of related attacks affecting domestic users, we'll recommend to all users to avoid clicking on unreliable links posted on social media, opening unreliable email attachments, running unreliable files with inflated names, and downloading unreliable apps. Additionally, it's critical to periodically update software patches and backup crucial files.
Threat Profile:
References:
The following reports contain further technical details: