Summary:
Security researchers have uncovered a resurgence of the new malware is ZLoader, also known as Terdot, DELoader, or Silent Night, is a modular trojan born from the leaked Zeus source code. It appears publicly in 2016 during a targeted campaign against German banks1, but its malicious activity traces back to at least August 2015. Zloader's malicious activities persisted until the start of 2018, only to reappear towards the end of 2019 under the moniker "Silent Night" in underground cybercriminal forums. The malware underwent substantial changes over time, ending in the development of version 2.0.0.0 around September 2021. Notably, like Qakbot, the threat actors leveraging Zloader shifted their focus from banking fraud to ransomware operations. Despite a temporary halt enforced by security researchers through a takedown operation in April 2022, Zloader recurred in September 2023 reemerged with a new iteration . Initially, this new version was labelled with the old version number 2.0.0.0. However, over the past several months, they released version 2.1.6.0 and 2.1.7.0.
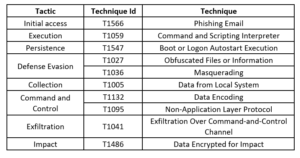
Zloader's latest version employs a spectrum of anti-analysis techniques to evade detection and delay reverse engineering efforts. These techniques include API import hashing, junk code insertion, filename-based anti-sandbox checks, and string obfuscation. The malware's modular architecture facilitates dynamic resolution of imported functions, enhancing its resilience against static analysis. Moreover, Zloader's static configuration, encrypted using RC4, now integrates an RSA public key for network encryption, signalling a shift towards more robust cryptographic mechanisms. The domain generation algorithm (DGA) has also been revamped to generate 32 domains daily, while network communications leverage HTTP POST requests with 1,024-bit RSA and RC4 encryption, coupled with the Zeus BinStorage format for message encapsulation. These enhancements collectively fortify Zloader's capabilities and pose significant challenges to cybersecurity professionals striving to combat its proliferation.
The resurgence of Zloader underscores its continuing threat to cybersecurity despite previous takedown efforts. The latest iteration of Zloader exhibits a difficult evolution marked by enhanced obfuscation techniques, revised DGA, and strengthened network encryption mechanisms. These advancements underscore the adaptability and persistence of threat actors behind Zloader, indicating a new wave of ransomware attacks and financial fraud schemes. As Zloader continues to evolve, cybersecurity stakeholders must remain vigilant and adopt proactive Defense measures to mitigate its impact and safeguard critical infrastructure and sensitive data from exploitation.
Threat Profile:
References:
The following reports contain further technical details:
https://thehackernews.com/2024/01/new-zloader-malware-variant-surfaces.html