Summary:
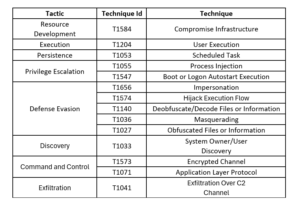
Researchers has identified a sophisticated cyber operation targeting European Union diplomats with a misleading wine-tasting event by undisclosed threat actor, identified as SPIKEDWINE. It’s primary goal is to disrupt geopolitical relations between India and Europe through the deployment of a modular backdoor named WINELOADER. The employed method involves the distribution of a PDF file disguised as an invitation letter from the Ambassador of India, ostensibly inviting diplomats to a wine-tasting event scheduled for February 2024. The PDF link leads recipients to a forged questionnaire, redirecting them to a malicious ZIP archive hosted on a compromised website, thus initiating the infection sequence.
This ZIP archive contains an HTA file housing obfuscated JavaScript code, facilitating the retrieval of an encoded ZIP archive containing WINELOADER from the same domain. WINELOADER is equipped with a core module designed to execute commands from the Command and Control (C2) server, inject itself into a dynamic-link library (DLL), and adjust the sleep interval between beacon requests. To enhance its covert operations, the SPIKEDWINE threat actor encrypts the core module, subsequent modules downloaded from the C2 server, and all related strings and data exchanges with a fixed 256-byte RC4 key. SPIKEDWINE has taken additional measures to avoid detection, employing advanced backdoor techniques such as re-encryption and memory buffer zeroing to safeguard sensitive data within the system's memory and thwart memory forensics solutions. Noteworthy is SPIKEDWINE's use of compromised network infrastructure at every stage of the attack chain.
The sophisticated attack, carried out by the SPIKEDWINE threat actor, demonstrated advanced tactics to exploit diplomatic tensions. While the attack remains unattributed to any known nation-state actor, researchers continue to monitor developments and provide necessary protections against such threats, underscoring the importance of proactive threat detection and mitigation strategies. Implement robust network traffic monitoring systems with anomaly detection capabilities to identify and respond promptly to any unusual activities, especially those related to compromised network infrastructure used by threat actors.
Threat Profile:
References:
The following reports contain further technical details: