Summary:
The Hacker against Apache Tomcat servers, focusing on the Mirai botnet campaign. The begins by presenting statistics and examples of recent attacks, indicating the widespread usage of Apache Tomcat in the cloud, big data, and website development. It then delves into a detailed analysis of a specific attack directed at one of the Apache Tomcat honeypots.
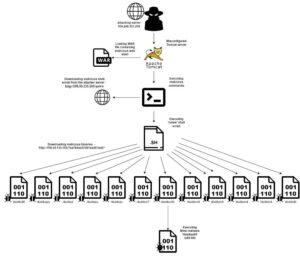
Execution Flow
The analysis reveals that the attacks exploited misconfigurations in the Tomcat web application manager, particularly weak user and password combinations. The attackers conducted brute force attacks on the manager app to guess the password. One of the honeypots used the default credentials (tomcat:tomcat), which facilitated the attackers' access. The attack flow is described, starting from the initial access phase, where the threat actor gains access to the web application manager. Once in control, the attacker deploys a malicious web shell, allowing remote code execution on the server. The web shell named 'cmd.jsp' enables the threat actor to execute commands on the Tomcat server. The attacker then downloads and executes the 'neww' shell script, which downloads and runs the Mirai malware, specifically designed for x86-64 systems. The Mirai malware is known for executing commands on behalf of a remote controller and could be used for various types of attacks, from cryptomining to severe DDoS campaigns.
The threat actor attempts to remove the command history file and conceal their actions. The impact of the attack is significant, as the compromised system becomes part of the Mirai botnet and is used for further malicious activities. the importance of detecting compromised workloads in runtime. Aqua's Cloud Native Detection and Response tool is mentioned, which leverages eBPF technology to detect malicious events at the Linux kernel level.
Overall, the prevalent usage of Apache Tomcat and the vulnerabilities that threat actors exploit to gain unauthorized access and carry out malicious activities, particularly through the Mirai botnet campaign. It emphasizes the need for vigilance and robust security measures to protect against such attacks.
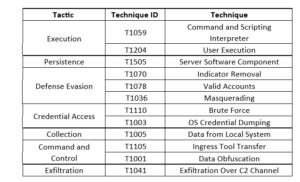
Threat Profile:
References:
The following reports contain further technical details:
https://thehackernews.com/2023/07/hackers-target-apache-tomcat-servers.html