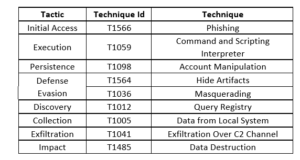
Summary:
Since December 22nd, 2022, threat actors have been exploiting a new tactic in their malware distribution campaigns by utilizing phishing emails with OneNote attachments. Unlike Microsoft Word or Excel, OneNote does not support macros, which previously served as a common method for launching malicious scripts and installing malware. Leveraging this vulnerability, threat actors have been targeting end users, luring them into opening OneNote attachments that initiate the execution of harmful processes. This analysis sheds light on the tactics, techniques, and procedures (TTP’s) employed in these attacks, such as the use of PowerShell.exe and Curl.exe to execute malicious scripts and establish connections with external sites for malware installation. By understanding the attack methods, organizations can better prepare and defend against this emerging threat.
During our investigation, we detected a concerning increase in malware originating from phishing emails with .one file attachments, primarily distributed through Outlook. Upon opening the OneNote attachment, the malware launches its attack. This method bypasses the common macros-reliant approach and capitalizes on the end user's unsuspecting nature. The attack begins with the execution of PowerShell.exe and Curl.exe. These tools allow the threat actors to run malicious scripts and establish connections with an external domain, minaato[.]com. The domain was found to be a file-sharing website, indicating a potential source for additional malicious indicators. Further examination revealed a chain of processes involving mshta.exe, curl.exe, and onenote.exe, each with specific behavioral attributes. These attributes were designed to evade detection and trigger alerts in security solutions, which is known for its heuristic-based alerting capabilities. Throughout the investigation, we encountered additional malicious files, including Cancellation[.]one, exhibiting similar activity and behavior as the initial .one file. The attackers seem to be refining their tactics and leveraging multiple files to maximize their chances of success.
From an attacker's perspective, the phishing emails with OneNote attachments provide an effective means to distribute malware. Exploiting the absence of macros in OneNote, threat actors trick end users into opening seemingly benign files, leading to the execution of malicious scripts. By utilizing PowerShell.exe and Curl.exe, the attackers establish connections to external domains, facilitating the installation and execution of malware.
Threat Profile:
References:
The following reports contain further technical details: