Summary:
Researchers recently discovered on Legion, a new Python-based credential harvester and hacktool designed to misuse multiple services for email. The utility comprises a variety of modules and is sold through the Telegram messenger. The malware targets different services to collect passwords, including AWS SNS, S3 and SES-specific credentials, Stripe/PayPal, Nexmo, Twilio, SMTP credentials, Tokbox, CPanel, WHM, PhpMyAdmin, and MessageBird. It is believed that the malware is a member of the AndroxGh0st malware family. Researchers also came upon a YouTube channel called "Forza Tools," which offered several Legion tutorial videos. These tools' developers frequently plagiarise one another's code, which makes assigning responsibility to a specific organisation challenging.
The primary targets of the Legion credential harvester are web servers running content management systems, PHP, or PHP-based frameworks, like Laravel. The tool uses a number of RegEx patterns to retrieve passwords for various web services from these targeted hosts. Credentials for email providers, cloud service providers (AWS), server management systems, databases, and payment systems, including Stripe and PayPal, are among them. The malware also has code for embedding webshells, brute forcing CPanel or Amazon accounts, and sending SMS messages to a list of randomly generated US cell numbers. Several techniques are available in Legion for obtaining login information from erroneous web servers. The malware will make an effort to request pages known to contain secrets, parse them, and save the secrets into results files sorted on an individual service basis, depending on the web server software, scripting language, or framework the server is using.
The Legion malware is a dangerous tool that can compromise SMTP and SMS spam operation services. Delivering spam SMS messages to American mobile network subscribers is one of Legion's features. Another feature is the capacity to register a webshell or remotely run malicious code by taking advantage of well-known PHP vulnerabilities. The quantity of users in the Telegram groups where it is promoted indicates that it has a sizable audience. The existence of comments written in Indonesian in the code raises the possibility that the developer is based in Indonesia.
Threat Profile:
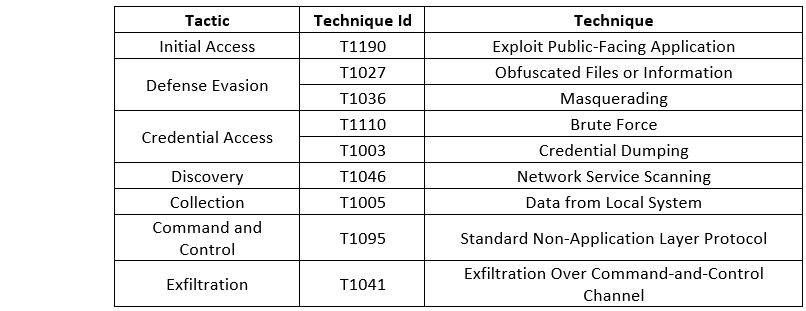
References:
The following reports contain further technical details:
https://thehackernews.com/2023/04/new-python-based-legion-hacking-tool.html