Summary:
The National Security Agency (NSA) and cybersecurity partner agencies issued an advisory today recommending system administrators to use PowerShell to prevent and detect malicious activity on Windows machines. PowerShell is frequently used in cyberattacks, leveraged mostly in the post-exploitation stage, but the security capabilities embedded in Microsoft’s automation and configuration tool can also benefit defenders in their forensics efforts, improve incident response, and to automate repetitive tasks.
Description:
The NSA and cyber security centres have created a set of recommendations for using PowerShell to mitigate cyber threats instead of removing or disabling it, which would lower defensive capabilities. Blocking PowerShell hinders defensive capabilities that current versions of PowerShell can provide and prevent components of the windows operating system from running properly. Recent version of PowerShell with improved capabilities and options can assist defenders in countering abuse of PowerShell. Proper configuration of WDAC or AppLocker on windows 10+ helps to prevent a malicious actor from gaining full control over a PowerShell session and the host.
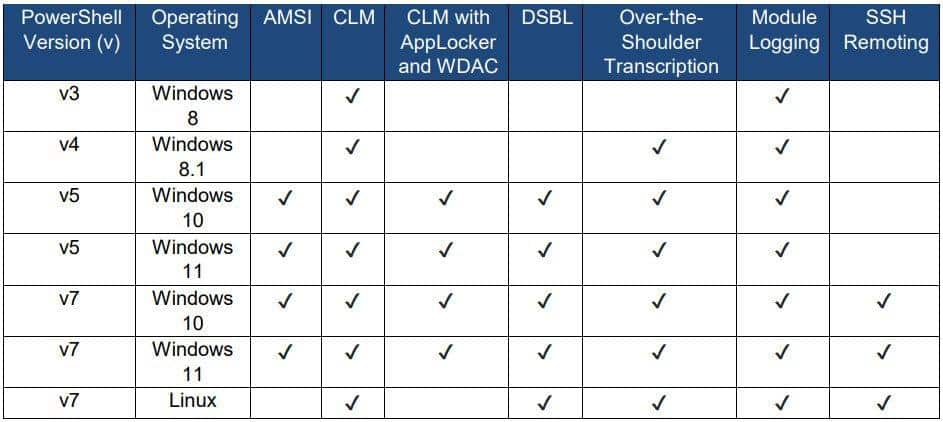
Best Practices:
Threat Assessment:
PowerShell is essential to secure the Windows operating system, particularly the newer versions that dealt away with previous limitations. When properly configured and managed, PowerShell can be a reliable tool for system maintenance, forensics, automation, and security.