Summary:
During the last week of July 2022, a ransomware infection was triggered in a user environment. Analyzing the sequence, it was found that a code-signed driver called “mhyprot2.sys”, which provides the anti-cheat functions for Genshin Impact as a device driver was being abused to bypass privileges. As a result, commands from kernel mode killed the endpoint protection processes. This ransomware was simply the first instance of malicious activity we noted. The threat actor aimed to deploy ransomware within the victim’s device and then spread the infection. Since mhyprot2.sys can be integrated into any malware, we are continuing investigations to determine the scope of the driver. The earliest evidence of compromise was a secretsdump from an unidentified endpoint of the targeted organization to one of the domain controllers. It was followed by the execution of discovery commands using wmiexec in the context of the built-in domain administrator account.
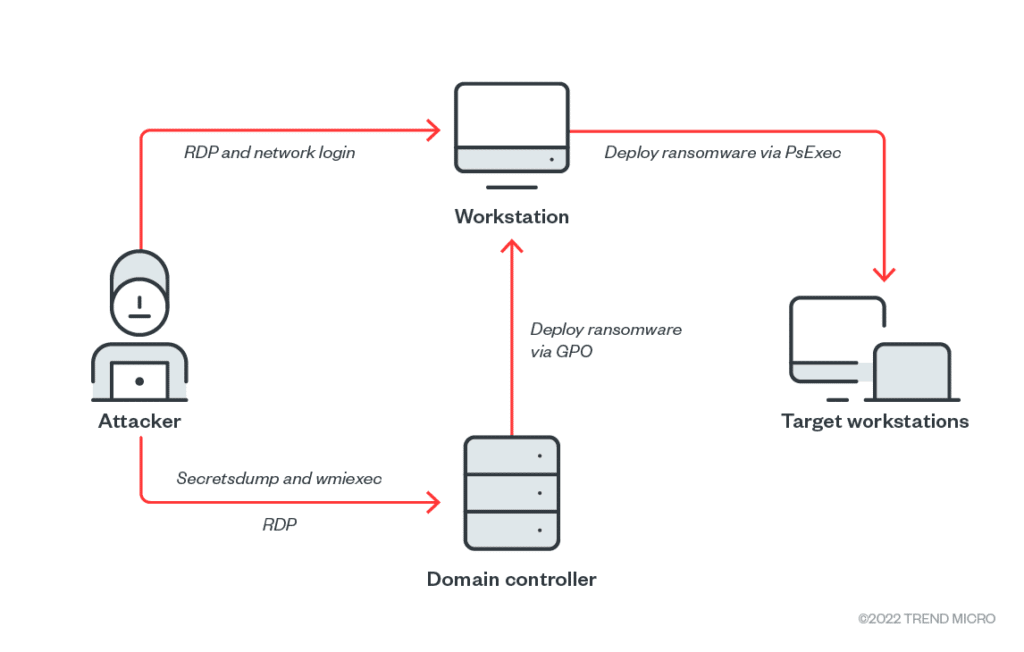
Figure : Attack overview
References:
The following reports contain further technical details: