Summary:
Researchers delves into the emergent landscape of Remote Access Trojan development, focusing on the Silver RAT v1.0, a Windows-based RAT written in C Sharp. The threat actor behind this malware, operating under the alias 'noradlb1' and associated with the group 'Anonymous Arabic,' showcases an active and sophisticated presence on hacker forums, social media platforms, and Telegram channels. The RAT boasts capabilities such as bypassing anti-viruses, launching hidden applications, keylogging, and data encryption using ransomware.
Silver RAT v1.0, a sophisticated Windows-based RAT written in C Sharp, exhibits a wide array of malicious functionalities. The RAT builder provides threat actors with the ability to customize payloads, with options ranging from bypassing antivirus detection to concealing processes. Noteworthy features include a Windows defender exclusion function, allowing the malware to evade detection after the initial launch, and the capability to erase all system restore points, rendering attempts at system recovery ineffective. Furthermore, the builder allows for the delayed execution of the payload, enabling threat actors to time their attacks strategically. The payload size dynamically adjusts based on selected options and can be delivered through various social engineering methods. The .Net executable payload, once executed, establishes a connection to an attacker-controlled panel, granting them a range of malicious capabilities over the compromised system.
The Silver RAT v1.0's command and control panel empower attackers to initiate diverse malicious activities. The 'Manager' option enables control over installed applications, file systems, registry keys, startup items, and system performance monitoring. Additionally, the RAT offers features such as hidden applications, hidden browsers, and hidden VNC (Virtual Network Computing), providing attackers with discreet control over the victim's system.
Researchers concludes that the threat actor 'noradlb1,' associated with 'Anonymous Arabic,' actively distributes Silver RAT v1.0 through multiple channels. The actor's involvement in various forums, social media platforms, and the clearnet underscores the potential widespread distribution of the malware. The developers, 'Dangerous silver' and 'Monstermc,' associated with S500 RAT and Silver RAT, operate an extensive network offering malware-as-a-service. As the threat landscape evolves, the researchers suggest organizations enhance their defense mechanisms, emphasizing security awareness training, regular updates, and strategic incident response plans to counter potential threats posed by Silver RAT and similar malicious tools.
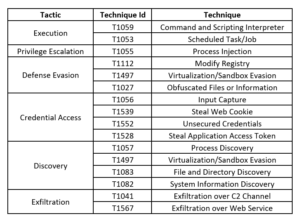
Threat Profile:
References:
The following reports contain further technical details: