Summary:
Storm-0558 is a China-based threat actor that has been engaging in espionage activities. Storm-0558 utilized forged authentication tokens to gain unauthorized access to user emails in approximately 25 organizations, including government agencies and consumer accounts in the public cloud. Storm-0558 operates with espionage objectives and exhibits methods consistent with other Chinese threat groups. While there are some overlaps with groups like Violet Typhoon (ZIRCONIUM, APT31), Storm-0558 is considered a distinct entity. The actor's working patterns align with typical working hours in China, indicating a geographical connection.
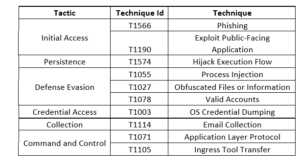
Researchers have observed Storm-0558 obtaining initial access through phishing campaigns and exploiting vulnerabilities in public-facing applications. Once access is gained, the threat actor collects credentials from various sources and signs into compromised users' cloud email accounts to extract information. Storm-0558 demonstrates a high level of technical expertise, displaying knowledge of target environments, authentication techniques, and application vulnerabilities. Researchers were alerted to anomalous Exchange Online data access, which was attributed to Storm-0558 based on its previous tactics, techniques, and procedures (TTPs). The investigation revealed that the threat actor was using forged Azure Active Directory (Azure AD) tokens to access customer Exchange Online data through Outlook Web Access (OWA).
Researchers determined that Storm-0558 had acquired a Microsoft account (MSA) consumer signing key and was utilizing it to forge authentication tokens. This key was intended for MSA accounts but had a validation error that allowed it to be trusted for signing Azure AD tokens. Authentication tokens are used to validate the identity of entities requesting access to resources such as email. Storm-0558 exploited the flawed token validation process to create falsified tokens with valid signatures, tricking relying parties into trusting them. The threat actor leverages PowerShell and Python scripts to perform REST API calls against the OWA Exchange Store service, allowing them to download emails, attachments, and conversations, and gather folder information. The actor employs proxy infrastructure, particularly the SoftEther VPN software, to obfuscate their activities.
Storm-0558, a China-based threat actor with espionage objectives, utilized forged authentication tokens to gain unauthorized access to user emails in targeted organizations. Storm-0558 has demonstrated technical expertise, targeted a range of entities, and utilized various intrusion techniques.
Threat Profile:
References:
The following reports contain further technical details: