Summary:
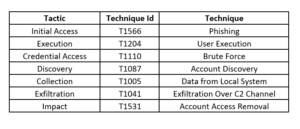
DRACOON Phishing Campaign.The uncovered phishing campaign reveals a sophisticated attack leveraging DRACOON.team, a reputable file-sharing solution, to deceive victims into accessing malicious links. The attackers exploit the trust associated with emails from known suppliers, increasing the effectiveness of their phishing emails. The use of DRACOON.team allows them to host PDF documents, containing secondary links leading to an attacker-controlled reverse proxy posing as a Microsoft 365 login portal. This innovative approach helps bypass traditional email security measures, as the initial link appears legitimate, and no files are delivered to the victim's endpoint. The compromised credentials and session cookies harvested through this method enable attackers to circumvent multi-factor authentication (MFA).
The phishing email, seemingly originating from a trusted supplier, includes a link redirecting to a PDF file on DRACOON.team. Within the PDF, a secondary link directs victims to a fake Microsoft 365 login page. The associated JavaScript file is obfuscated and, when deobfuscated, reveals its role in credential harvesting. The stolen credentials are then uploaded to an undisclosed webpage. Analysis of Microsoft 365 sign-in events and MFA logs identifies the presence of a reverse proxy, aiding in the identification of compromised accounts. The investigation also highlights additional phishing links within the campaign, using various subject lines to lure victims.
The phishing attack underscores the limitations of MFA against advanced threats like EvilProxy attacks. The use of DRACOON.team enhances attackers' capabilities, exploiting legitimate file-sharing services to improve success rates and evade detection. The incident emphasizes that emails from trusted sources do not guarantee legitimacy, urging users to exercise caution. The researcher concludes with proactive mitigation strategies, emphasizing security awareness, phishing-resistant MFA, robust email security, and continuous monitoring to strengthen overall cybersecurity posture. The incident serves as a stark reminder that vigilance and a multi-layered security approach are crucial in defending against evolving phishing threats.
Threat Profile:
References:
The following reports contain further technical details: