| Summary: |
Researcher are initiated an intelligence collection operation to decode the makeovers of a threat group called DuckTail. Over a three-month period, they gathered critical information about DuckTail's operational framework, shedding light on its intrusion techniques, compromise tactics, and post-compromise procedures. DuckTail primarily targets users in the digital marketing and advertising sector, exploiting themes like AI tools to infect devices.

Infection Flow
DuckTail's main objective is to gain access to social media business accounts, particularly those belonging to digital marketers. They use a variety of distribution methods, with social engineering through LinkedIn messaging being a primary vector. The threat actors create fake LinkedIn recruiter profiles and job postings impersonating popular companies to lure victims. The malware associated with DuckTail steals session cookies from web browsers, specifically tailored for taking over Facebook business accounts. They also target TikTok business accounts and Google ad accounts. To distribute their malware, DuckTail leverages various cloud services and URL shortening services, making it challenging to detect their malicious activities. They exploit themes related to popular AI tools like ChatGPT and Google BardAI to trick victims into installing malicious software.
The threat actors use private residential proxy services to log into compromised social media business accounts, avoiding detection. They also abuse the "Encrypted notifications" feature on Facebook to hinder victim account recovery. DuckTail's stolen social media accounts feed an underground market, where they are sold based on their perceived value. The blog provides insights into their strategies, such as adding their email addresses to compromised accounts and using compromised LinkedIn accounts for communication.
Overall, DuckTail is a sophisticated and evolving cyber threat operation that targets digital marketing and advertising professionals, using social engineering and advanced techniques to compromise and profit from their accounts in an underground market.
| Threat Profile: |
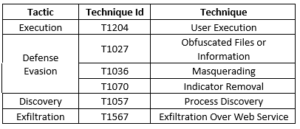
| References:
The following reports contain further technical details: https://thehackernews.com/2023/09/vietnamese-cybercriminals-targeting.html |